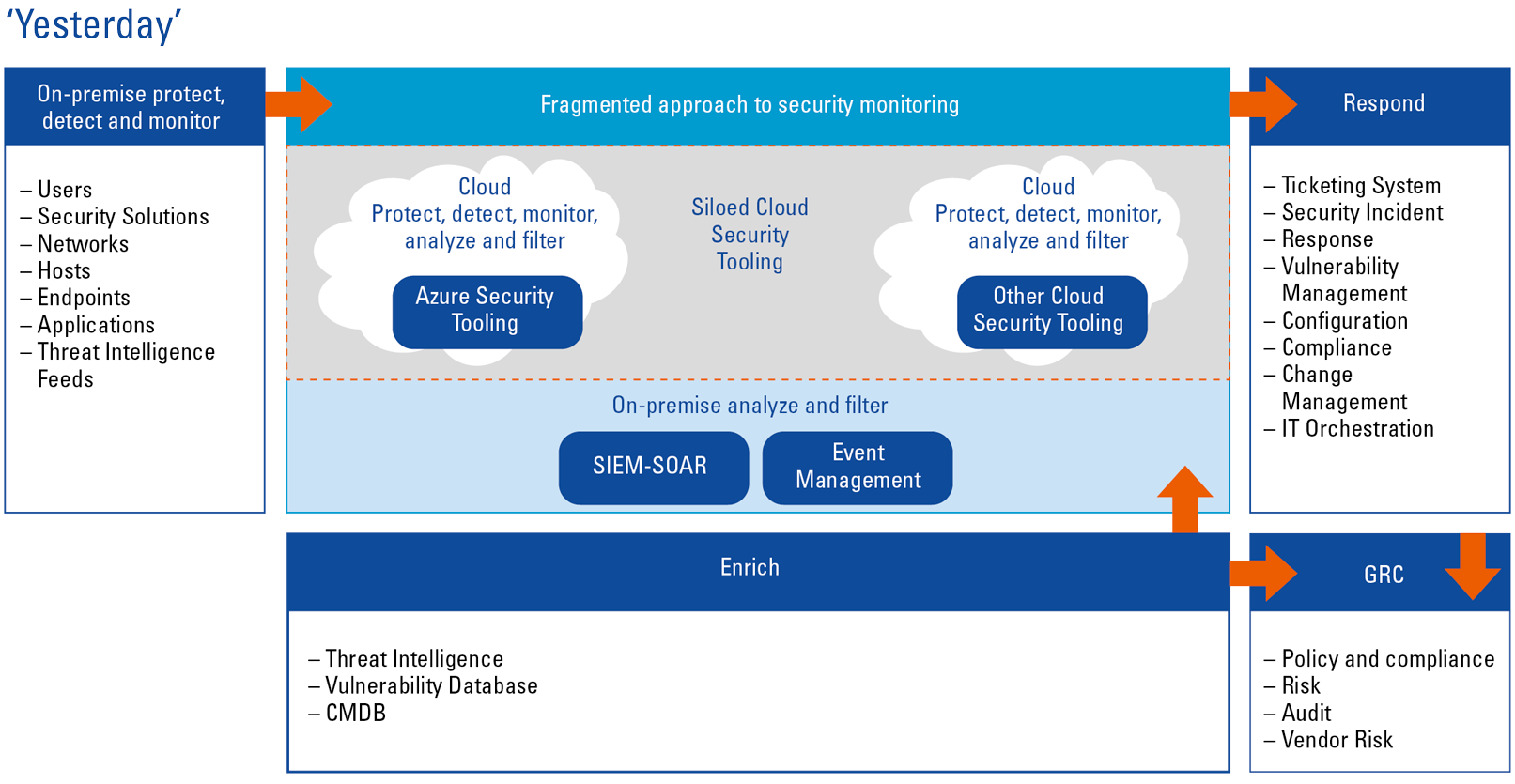
Top 22 Security Information and Event Management Software in 2021 - Reviews, Features, Pricing, Comparison - PAT RESEARCH: B2B Reviews, Buying Guides & Best Practices

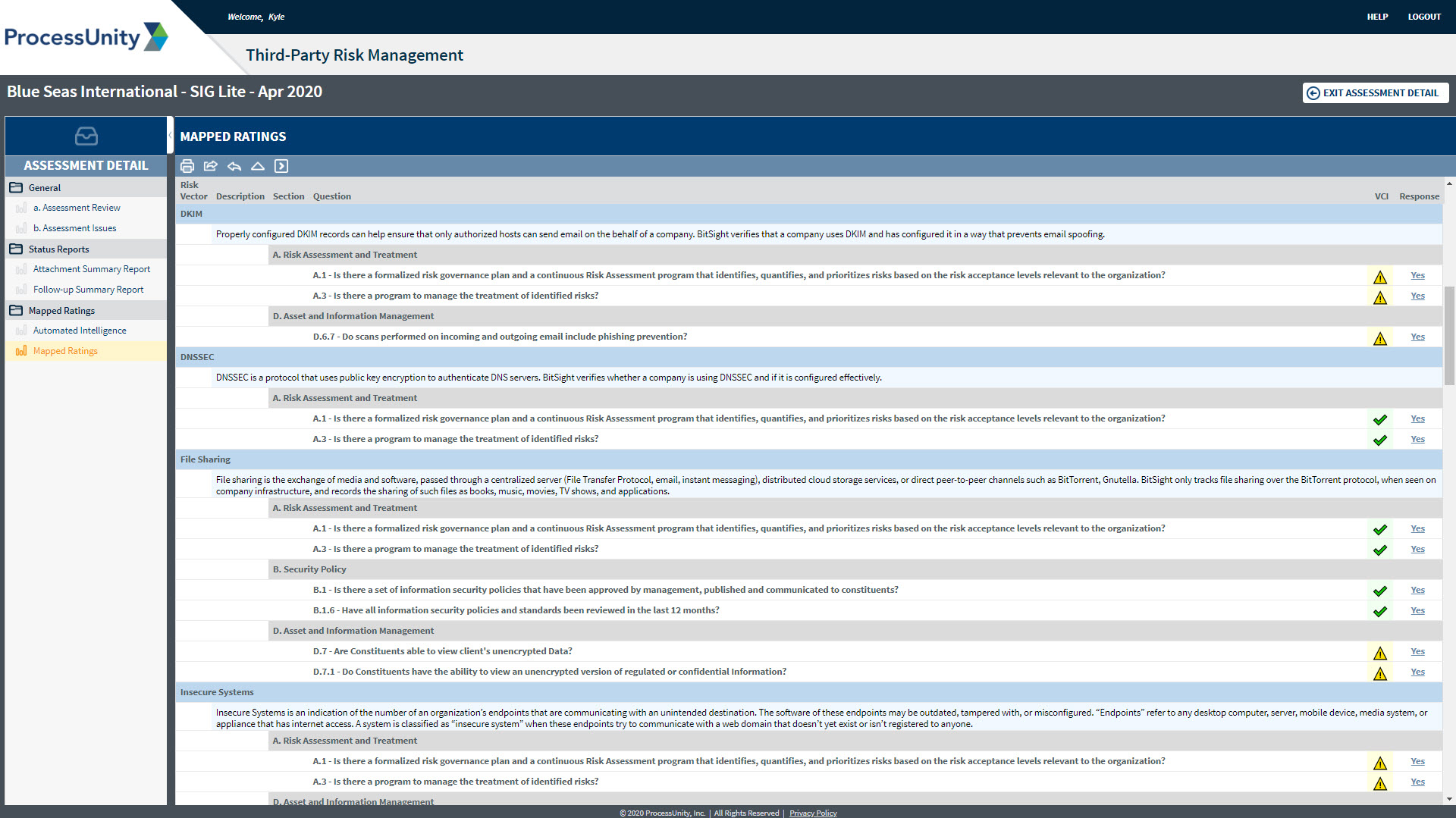
BitSight | Continuous Third-Party Security Monitoring Powers Business Objectives & Vendor Accountability